Responder: An Overview of a Powerful Network Analysis Tool
Responder is a robust and versatile network analysis tool designed for penetration testing and security assessments. Developed in Python, it specializes in identifying and exploiting vulnerabilities within network protocols, making it an invaluable asset for security professionals seeking to fortify their network defenses. Here’s a brief overview of Responder’s key features and capabilities: 1. […]
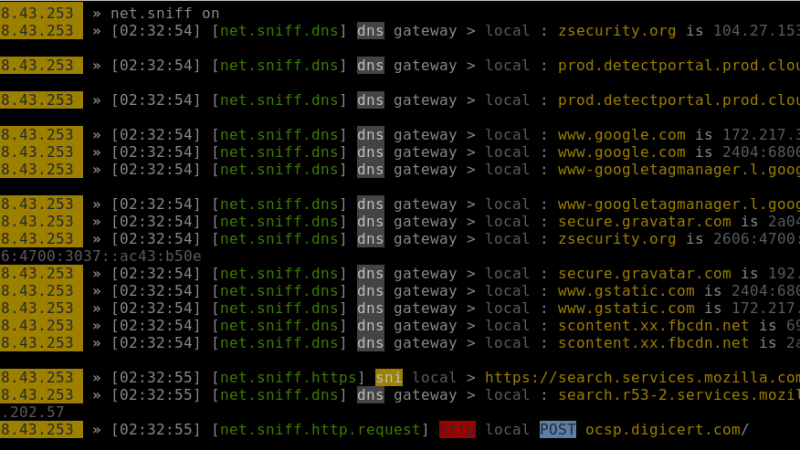
Sniffing using bettercap in Linux
Sniffing is the process of capturing and monitoring data packets that are passed through the network. It is used to capture the data of the victim and bettercap is a powerful tool used to perform various MITM(man in the middle) attacks on a network. Also, ARP Spoofing is a type of attack in which an […]
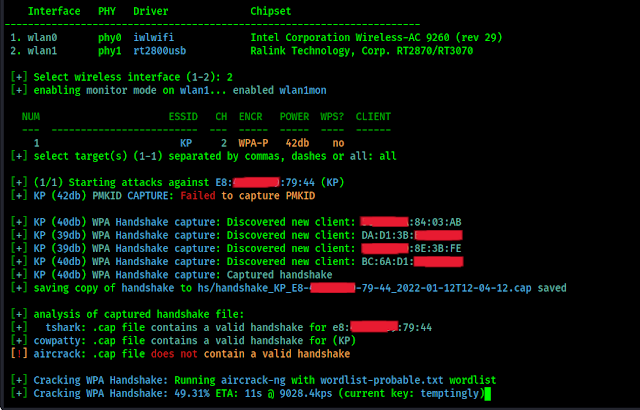
WiFite: A Powerful Tool for Wi-Fi Penetration Testing
# Exploring WiFite: A Powerful Tool for Wi-Fi Penetration Testing In the realm of cybersecurity, the importance of securing wireless networks cannot be overstated. As technology advances, so do the tools available to both security professionals and malicious actors. WiFite, a powerful and versatile Wi-Fi penetration testing tool, stands out as an essential asset for […]
How to Use Hydra to Hack Passwords With Examples
In the realm of ethical hacking, security professionals leverage various tools to test and strengthen the security posture of systems and networks. One such powerful tool is Hydra, a password-cracking tool designed to assist in identifying vulnerabilities related to weak or compromised credentials. In this article, we’ll delve into Hydra, its capabilities, and provide some […]
Web Shell Mastery: Weevely Commands Demystified in Kali Linux
## What is Weevely? Weevely is a web shell that enables remote administration of web servers. Its lightweight design and simple deployment make it an excellent choice for penetration testers aiming to maintain access to a compromised system without being detected easily. ### Installation of Weevely in Kali Linux: Before exploring the example commands, […]
Mastering Wi-Fi Security with Wifite: A Comprehensive Guide with 30+ Examples
Introduction: Securing your Wi-Fi network is a critical aspect of maintaining a safe and private online environment. Wifite, a powerful and versatile Wi-Fi auditing tool, is designed to help users test the security of their wireless networks. In this comprehensive guide, we will explore the features of Wifite and provide over 30 examples to demonstrate […]
Unveiling the Secrets of Nmap
In the ever-evolving landscape of cybersecurity, tools that empower professionals to assess and secure networks are invaluable. Among these, Nmap stands tall as a versatile and powerful network scanning tool. Network Mapper, commonly known as Nmap, is an open-source tool used for network exploration and security auditing. In this article, we will delve into […]
FFUF (short for “Fuzz Faster U Fool”) is a fast web fuzzer
`ffuf` (short for “Fuzz Faster U Fool”) is a fast web fuzzer used for discovering hidden resources and web vulnerabilities by bruteforcing various parts of a web application. Here are some examples of how to use `ffuf`: 1. Basic Directory Fuzzing: ffuf -u http://example.com/FUZZ -w common.txt This command will perform directory fuzzing by replacing `FUZZ` […]