An Inclusive Personal Portfolio and Blog for Cyber Aspirants
Hi, I'm Shaik Saimeera
into
CyberSecurity.
Web Development.
Cloud Computing
Open Source
I am Shaik Saimeera, a Linux server administrator, cybersecurity expert, and IT strategist with extensive experience in server management, web hosting solutions, and cybersecurity. Over the years, I have built, optimized, and secured countless server infrastructures, ensuring high availability, scalability, and protection against cyber threats. My expertise spans a wide range of technologies, from cloud computing and virtualization to penetration testing and AI-driven security automation.

What I Do
Installation & Configuration
Effortlessly handle server installation and configuration, including cPanel, Plesk, and other hosting platforms.
Server Management
Seamless server management ensuring optimal performance, security, and reliability for your digital infrastructure.
Server Hardening
Disaster recovery: Building resilience, safeguarding data, and ensuring business continuity in unforeseen crises.
Disaster Recovery
I throw myself down among the tall grass by the stream as Ilie close to the earth.
Vuln, Assesment
Vulnerability assessment: Identifying weaknesses to fortify digital defenses and enhance overall security.
Web Developer
Web developer: Crafting digital experiences, turning ideas into interactive websites, and driving online innovation.
My Resume
Education Quality
NTR UHS
BSC MLT (jun 2016 - jun 2020)I attended NTRUHS and completed my BSC from June 2016to June 2020, focusing on Biology, Physics, and Chemistry as part of my academic journey.
Chaitanya college
Intermediate BiPC (jun 2014 - jun 2016)I attended Chaitanya College and completed my BiPC program from June 2014 to June 2016, focusing on Biology, Physics, and Chemistry as part of my academic journey.
ZP High School
10 th Class (jun 2009 - jun 2014)I completed my 10th grade at ZP High School Magallu from June 2009 to June 2014, marking a significant milestone in my education.
Job Experience
Logical Web SOlutions
Owner - (From 2022)A popular destination with a growing number of highly qualified homegrown graduates, it's true that securing a role in Malaysia isn't easy.
TrustedHosting.in
Linux Server Administrator (2021 - Present )I have been employed as a Linux Server Administrator at TrustedHosting.in in the web hosting industry since 2021, contributing to server management and operations.
Professional Skill
cPanel
Plesk
Direct Admin
Linux
Penetration Testing
Development Skill
WHMCS
WordPress
HTML
PHP
Python
Linux System Administrator
TrustedHosting.in - (Jan 2021 - Present Working)• Experienced cPanel & Plesk Server Administrator with a proven track record of managing and optimizing web hosting environments for maximum performance and uptime.
Vuln , Assessment
Web Developement
• Weaving innovation, design, and technology into a seamless user journey.Transforming pixels into meaningful experiences for global audiences.
Disaster Recovery
• Expert in implementing backup and disaster recovery strategies, ensuring the protection and availability of critical website data and assets.

Earning the “Offensive Pentesting” certification from TryHackMe is a notable achievement in the field of cybersecurity. This certification signifies expertise in conducting offensive security assessments, emulating real-world cyberattacks, and identifying vulnerabilities to help organizations bolster their defenses.
To obtain this certification, I completed an intensive training program that covered a wide range of offensive penetration testing techniques, tools, and methodologies. I gained practical experience by solving complex challenges and engaging in simulated scenarios provided by TryHackMe.
The “Offensive Pentesting” certification highlights my capability to assess and enhance security postures, identify vulnerabilities, and provide actionable recommendations to strengthen an organization’s cybersecurity defenses. It underscores my dedication to mastering ethical hacking practices and staying updated with the latest security threats and countermeasures.


Red Teaming From TryHackMe
Earning the “Red Teaming” certification from TryHackMe is a distinguished accomplishment in the realm of cybersecurity. This certification acknowledges expertise in advanced penetration testing techniques, ethical hacking, and simulating real-world attacks to assess and improve an organization’s security posture.
To achieve this certification, I undertook an intensive training program that encompassed a broad spectrum of red teaming activities, including advanced exploitation, social engineering, post-exploitation, and lateral movement. I also gained hands-on experience by applying these skills in various practical scenarios provided by TryHackMe.
The “Red Teaming” certification demonstrates my capability to mimic sophisticated adversaries, identify security weaknesses, and provide strategic recommendations to enhance an organization’s defenses. It reflects my commitment to mastering cutting-edge offensive security tactics and ensuring robust security measures are in place to protect digital assets.
As a certified Red Teamer, I am well-prepared to assist organizations in proactively defending against cyber threats, conducting comprehensive security assessments, and helping them stay one step ahead of potential attackers. This certification underscores my dedication to maintaining the highest standards of ethical hacking and cybersecurity practices.


Security Engineer From TryHackMe
Through a wide variety of mobile applications, we’ve developed a unique visual system.
Earning the “Security Engineer” certification from TryHackMe is a significant achievement in the realm of cybersecurity. This certification validates expertise in designing, implementing, and managing security measures to protect digital assets effectively.
The “Security Engineer” certification signifies my ability to analyze and enhance security postures, mitigate risks, and respond to security incidents proficiently. It reflects my commitment to staying updated with the evolving threat landscape and implementing robust security solutions to safeguard organizations’ data and systems.
As a certified Security Engineer, I am well-equipped to address complex security challenges, fortify defenses against cyber threats, and contribute to maintaining the confidentiality, integrity, and availability of critical information in an ever-changing digital environment.


Jr. Penetration Tester + From TryHackMe
Earning the “Jr. Penetration Tester” certification from TryHackMe is a notable achievement in the field of cybersecurity and ethical hacking. This certification demonstrates proficiency in practical penetration testing techniques and hands-on experience with real-world security challenges.
To obtain this certification, I completed a series of challenges and labs on the TryHackMe platform, covering various aspects of penetration testing, such as network scanning, vulnerability assessment, and exploit development. I also learned about different attack vectors and how to secure systems against them.
The “Jr. Penetration Tester” certification showcases my ability to assess and secure computer systems, networks, and applications from potential threats and vulnerabilities. It reflects my commitment to acquiring practical skills and knowledge in ethical hacking and cybersecurity.
This certification is a stepping stone in my journey towards becoming a skilled penetration tester, capable of identifying and addressing security weaknesses in systems and helping organizations bolster their defenses against cyberattacks. It underscores my dedication to staying updated with the latest cybersecurity trends and best practices to protect digital assets effectively.


Comptia Pentest + From TryHackMe
Completing the CompTIA Pentest+ learning path certification from TryHackMe is a commendable achievement in the field of penetration testing and cybersecurity. This certification program equips individuals with the knowledge and skills needed to assess network vulnerabilities, perform penetration tests, and recommend security measures.
During this certification journey, I engaged in hands-on practical exercises and challenges offered by TryHackMe to develop a deep understanding of penetration testing methodologies, tools, and techniques. I learned how to identify and exploit vulnerabilities in various systems and networks ethically, ultimately helping organizations strengthen their security defenses.
The CompTIA Pentest+ certification from TryHackMe demonstrates my proficiency as a penetration tester, capable of conducting comprehensive security assessments, producing detailed reports, and aiding organizations in mitigating potential security risks. It showcases my commitment to maintaining the highest standards of ethical hacking and cybersecurity.
Overall, this certification underscores my expertise in penetration testing and my dedication to staying current with industry best practices, making me a valuable asset in the field of cybersecurity, where protecting digital assets from cyber threats is of paramount importance.


Pentesting Agent – Intermediate [EC-Council]
Through a wide variety of mobile applications, we’ve developed a unique visual system.
Earning the “Pentesting Agent Intermediate” certification from EC-Council’s CodeRed program is a notable achievement in the field of ethical hacking and penetration testing. This certification signifies expertise in conducting security assessments, identifying vulnerabilities, and mitigating risks in computer systems and networks.
The “Pentesting Agent Intermediate” certification demonstrates my capability to contribute to strengthening information security for organizations by identifying and addressing potential security vulnerabilities before malicious actors can exploit them. It reflects my commitment to upholding ethical hacking practices and safeguarding digital assets from cyber threats.
Overall, this certification underscores my expertise as an intermediate-level pentester, capable of assisting organizations in proactively defending against cyber threats and ensuring the confidentiality, integrity, and availability of their critical data and systems.

Date Of Completion : 26th Mar 2023
Certification ID : 863

LiteSpeed Web Server Admin.
Certified LiteSpeed Web Server Admin

Obtaining the LiteSpeed Web Server Admin Certification represents a significant achievement in the field of web hosting and server administration. This certification demonstrates a deep understanding of LiteSpeed’s high-performance web server software and the ability to effectively manage and optimize web server environments.
To earn this certification, I completed a comprehensivethat covered various aspects of LiteSpeed web server administration. This included configuring server settings, optimizing performance, implementing security measures, and troubleshooting common issues.
With this certification, I am well-equipped to enhance website loading speeds, handle increased web traffic efficiently, and ensure the security and reliability of web server environments. LiteSpeed’s advanced features, including HTTP/2 and QUIC support, make it a valuable asset for web hosting professionals aiming to provide top-notch service to clients.
Having the LiteSpeed Web Server Admin Certification validates my expertise in leveraging LiteSpeed technology to deliver exceptional web hosting solutions, ultimately benefiting websites and businesses by improving their online presence and user experience. It also underscores my commitment to staying current with industry-leading web server technologies and best practices.
Imunify 360 Certification
Certified Imunify 360 Admin.

Earning the Imunify360 certification in the field of cybersecurity was a significant accomplishment. Imunify360 is a comprehensive security solution designed to protect Linux servers from various cyber threats, making it a vital tool for any Linux Server Administrator.
The certification process involved a deep dive into the Imunify360 software suite, covering its features, functionalities, and how to effectively implement and manage security measures using this solution. I learned about its powerful intrusion detection and prevention system (IDS/IPS), its robust firewall capabilities, and its ability to protect against various types of malware, including web-based threats.
During the certification program, I gained valuable insights into real-time threat detection, mitigation techniques, and the importance of keeping server environments secure in the ever-evolving landscape of cybersecurity threats. I also became proficient in configuring and customizing Imunify360 to meet specific server security requirements, ensuring optimal protection for web hosting environments.
Earning the Imunify360 certification has not only enhanced my expertise as a Linux Server Administrator but also reinforced my commitment to safeguarding web hosting infrastructures against cyberattacks. This certification signifies my dedication to staying up-to-date with industry-leading security solutions, ultimately benefitting the web hosting industry and the clients I serve. It is a testament to my knowledge and skills in proactively defending against digital threats, ensuring the integrity and availability of critical online resources.
Date Of Certification : 08/23/2023 – 08/22/2024
ID : 6a89-d8ad-f4a3-ddde
WHM Administration Certification (CWA)
Through a wide variety of mobile applications, we’ve developed a unique visual system.
I earned the WHM Administration Certification (CWA) as a testament to my expertise in managing web hosting servers effectively. This certification, obtained through rigorous training and examination, demonstrates my proficiency in utilizing cPanel’s Web Host Manager (WHM), a powerful control panel widely used in the web hosting industry.
Throughout the certification process, I acquired in-depth knowledge of WHM’s functionalities, including server provisioning, resource allocation, security configuration, and domain management. I can efficiently create and manage hosting accounts, implement security measures, and troubleshoot server-related issues. This certification validates my ability to optimize server performance, ensure data integrity, and provide top-notch hosting services to clients.
Having earned the WHM Administration Certification, I am well-equipped to excel in the web hosting industry, delivering reliable server management, excellent customer support, and robust security solutions. My dedication to staying updated with the latest industry trends and technologies ensures that I can provide high-quality hosting services while maintaining the utmost security and efficiency for clients’ websites and data.

Date Of Completion : 08/24/2023 – 08/23/2024
Certification ID : e79f-f359-780b-2315
Blog
What is Plesk And How its Usefull
Plesk is a web hosting control panel that provides website owners with a centralized platform for managing their websites and

What is Plesk And How its Usefull
Plesk is a web hosting control panel that provides website owners with a centralized platform for managing their websites and servers. It offers a user-friendly interface, automation capabilities, and powerful tools for website management and security. In this article, we will take a closer look at what Plesk is, its features, and why it is so useful for website owners and hosting providers.
Plesk was first introduced in 2001 and has since become a popular choice for web hosting control panels. It is available for Windows and Linux servers and provides website owners with a range of tools and features for managing their websites and servers. Plesk provides a centralized location where website owners can manage their email accounts, FTP accounts, databases, and security features.
One of the key features of Plesk is its user-friendly interface. The software is designed to be easy to use, even for those with limited technical knowledge. With Plesk, website owners can easily create and manage their websites, email accounts, and databases. The software also provides a range of security tools, such as password protection for directories, SSL certificates, and firewalls, to help keep websites and data secure.
Another important feature of Plesk is its automation capabilities. The software automates many tasks that would otherwise need to be performed manually, such as backups and software updates. This saves website owners time and reduces the risk of errors. Plesk also integrates with a range of third-party applications and services, such as WordPress and Magento, making it easy for website owners to manage their website and server.
Plesk also provides detailed reporting and analytics, allowing website owners to monitor the performance of their website and server. The software provides detailed information on website traffic, resource usage, and error logs. This information is critical for website owners who want to optimize their website for performance and troubleshoot any issues that may arise.
In conclusion, Plesk is a powerful and flexible web hosting control panel that provides website owners with a centralized platform for managing their websites and servers. Its user-friendly interface, automation capabilities, and detailed reporting and analytics make it a popular choice among website owners and hosting providers. Whether you are just starting out with your website or have a large and complex website, Plesk provides the tools and features you need to manage your website with ease.
How to install whm panel in centos , ubuntu and debian.
WHM (Web Host Manager) is a control panel that allows web hosting providers to manage their servers, websites, and clients

How to install whm panel in centos , ubuntu and debian.
WHM (Web Host Manager) is a control panel that allows web hosting providers to manage their servers, websites, and clients more efficiently. The panel provides a user-friendly interface to manage various aspects of the server, including creating new hosting accounts, managing domains, setting up email accounts, and much more. In this article, we will explain the process of installing WHM on various Linux environments.
- Installing WHM on CentOS
CentOS is one of the most widely used Linux distributions for web hosting. To install WHM on CentOS, you need to have a VPS (Virtual Private Server) or dedicated server with CentOS 7 or 8 installed. The first step is to log in to your server as the root user. Next, run the following command to update the package list and upgrade the system:
yum update && yum upgrade
After the system is updated, run the following command to install the latest version of WHM:
cd /home && curl -o latest -L https://securedownloads.cpanel.net/latest && sh latest
The installation process will take some time, depending on the speed of your server. Once the installation is complete, you can access WHM by navigating to https://your-server-IP:2087 in your web browser. You will need to log in with your root username and password.
- Installing WHM on Ubuntu
Ubuntu is another popular Linux distribution used by web hosting providers. To install WHM on Ubuntu, you need to have a VPS or dedicated server with Ubuntu 18.04, 20.04, or 22.04 installed. The first step is to log in to your server as the root user. Next, run the following command to update the package list and upgrade the system:
apt update && apt upgrade
After the system is updated, run the following command to install the latest version of WHM:
cd /root && wget https://securedownloads.cpanel.net/latest && sh latest
The installation process will take some time, depending on the speed of your server. Once the installation is complete, you can access WHM by navigating to https://your-server-IP:2087 in your web browser. You will need to log in with your root username and password.
- Installing WHM on Debian
Debian is another widely used Linux distribution for web hosting. To install WHM on Debian, you need to have a VPS or dedicated server with Debian 9 or 10 installed. The first step is to log in to your server as the root user. Next, run the following command to update the package list and upgrade the system:
apt update && apt upgrade
After the system is updated, run the following command to install the latest version of WHM:
cd /root && wget https://securedownloads.cpanel.net/latest && sh latest
The installation process will take some time, depending on the speed of your server. Once the installation is complete, you can access WHM by navigating to https://your-server-IP:2087 in your web browser. You will need to log in with your root username and password.
In conclusion, WHM is a powerful control panel that can greatly simplify the task of managing a web hosting server. The installation process is straightforward and can be done on various Linux environments, including CentOS, Ubuntu, and Debian.
Top 5 Plugins To Protect WordPress Websites
Top 5 Plugins To Protect WordPress Websites Introduction: WordPress is a popular content management system powering millions of websites worldwide.

Top 5 Plugins To Protect WordPress Websites


Top 5 Plugins To Protect WordPress Websites
Introduction: WordPress is a popular content management system powering millions of websites worldwide. Unfortunately, its popularity also makes it an attractive target for hackers attempting brute force attacks. These attacks involve automated scripts that systematically guess usernames and passwords to gain unauthorized access to your website’s admin panel. To fortify your WordPress website against such threats, it is essential to employ effective security measures, including the right plugins. In this article, we will explore some essential plugins that can help protect your WordPress website from brute force attacks.
- Wordfence Security: Wordfence Security is a comprehensive security plugin for WordPress that offers powerful protection against brute force attacks. It includes features like login security, which limits login attempts and enforces strong passwords. Wordfence also incorporates a robust firewall that identifies and blocks malicious traffic in real-time. With its advanced malware scanner, this plugin can detect and remove potential threats, ensuring the integrity of your website.
- Login LockDown: Login LockDown is a lightweight yet effective plugin designed to prevent brute force attacks by restricting login attempts. It records IP addresses and timestamps of failed login attempts and blocks subsequent login requests from those IP addresses for a specified period. By limiting the number of login attempts, Login LockDown adds an extra layer of security to your website’s login page.
- All In One WP Security & Firewall: All In One WP Security & Firewall is a feature-rich plugin that provides comprehensive protection against brute force attacks. It offers a user-friendly interface with various security measures, including login lockdown, CAPTCHA support, and database security. The plugin also includes a firewall that filters malicious requests and protects against known attack patterns. With its extensive set of security features, All In One WP Security & Firewall enhances the overall security of your WordPress website.
- iThemes Security: Formerly known as Better WP Security, iThemes Security is another popular security plugin that offers robust protection against brute force attacks. It includes a range of security measures, such as two-factor authentication, brute force protection, and file change detection. iThemes Security also provides a strong password enforcement feature, ensuring that all users have secure login credentials.
- Limit Login Attempts Reloaded: Limit Login Attempts Reloaded is a lightweight plugin that allows you to define the number of login attempts before a user gets locked out. It helps protect your website from brute force attacks by restricting repeated login attempts from a single IP address. The plugin also provides an option to receive email notifications whenever an IP address gets locked out, enabling you to stay informed about potential security threats.
Conclusion: Brute force attacks pose a significant threat to WordPress websites, but implementing the right security measures can mitigate the risk. By utilizing plugins like Wordfence Security, Login LockDown, All In One WP Security & Firewall, iThemes Security, and Limit Login Attempts Reloaded, you can fortify your website against brute force attacks. Remember to keep your WordPress installation and plugins up to date, use strong and unique passwords, and regularly backup your website to ensure comprehensive security. Protecting your website from brute force attacks is an ongoing effort, and these plugins can be valuable assets in safeguarding your valuable online presence.
How To Install Lets Encrypt SSL Certificate On Cpanel
Setp 1 > Go To Cpanel And Search For Lets Encrypt Step 2 > The next step is to
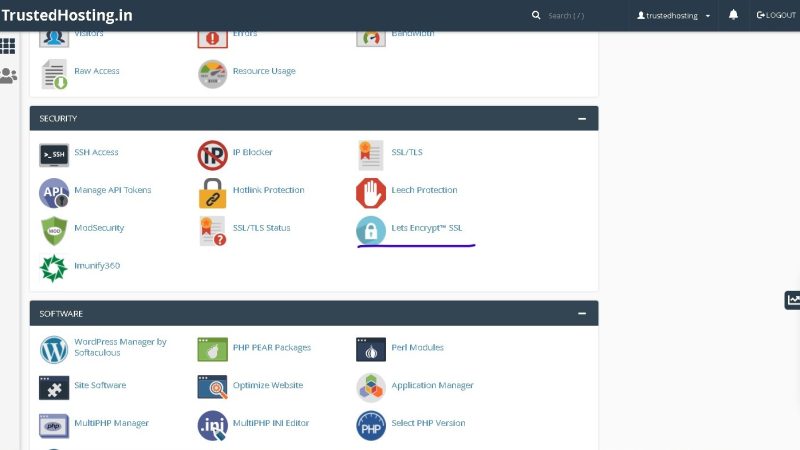
How To Install Lets Encrypt SSL Certificate On Cpanel
Setp 1 > Go To Cpanel And Search For Lets Encrypt
Step 2 > The next step is to issue a new SSL certificate for the desired domain name. Choose from one of your domains in the list then click ‘Issue‘ under Actions.
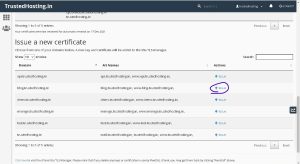
Step 3 >
In the next window, you will have multiple Domain options. For better understanding, we’ll explain each one.
Include Wildcard? – select this option only if you want to install a Let’s Encrypt Wildcard SSL which will cover *.yourdomain.com. To include wildcard domains, please make sure to choose first the dns-01 validation method.
Add cPanel subdomains? – to select some additional cPanel subdomains*. This is optional and it’s not a mandatory checkbox.
cPanel subdomains are those such as cpanel.* and webmail.*, which when added, allow access to cPanel services via that subdomain.
Step 4) Choose an SSL validation method:
http-01 – You will usually want to use the HTTP validation method.
dns-01 – If your domain’s nameservers point to cPanel, then you have the option of using the DNS validation method instead.

If you wish to issue wildcards, you MUST use the DNS validation method.
Step 5) Once you’ve chosen the validation method, click on the ‘Issue‘ button.
That’s it! The SSL certificate will be installed on your domain. The virtual host will be automatically updated with the new certificate and Apache will be restarted in the background.

Video Tutorial
How To Create Private /Child Nameservers At Godaddy
Register your own host names to create custom nameservers for your domains registered with GoDaddy. The maximum number of host

How To Create Private /Child Nameservers At Godaddy
Register your own host names to create custom nameservers for your domains registered with GoDaddy. The maximum number of host names you can add is determined by the TLD registry.
- Log in to your GoDaddy Domain Control Center. (Need help logging in? Find your username or password.)
- Select your domain to access the Domain Settings page.
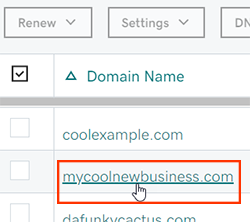
- Select Manage DNS under Additional Settings.
- Select Host Names from the
 More menu.
More menu.
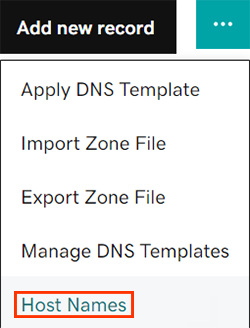
- Select ADD.
- Enter the Host name and IP Address in the appropriate fields. Don’t include your domain in the Host name field – it’s already added for you.
- Select Save when finished.
Your new host names will be ready to use within 90 minutes, in most cases. We’ll send you an email when they’re ready, then you can change your nameservers to use your new host names.
How To Create Private/Child Nameservers At Hostinger
You can manage your DNS records via DNS Zone Editor. To add a new child nameservers records, open the Domains

How To Create Private/Child Nameservers At Hostinger
You can manage your DNS records via DNS Zone Editor. To add a new child nameservers records, open the Domains tab, choose the domain, for which you want to apply changes, and reach DNS / Nameservers page:
There select Child nameservers:
To create child nameservers, all you need to do:
-
Insert nameservers name
-
Insert nameservers IP
-
Save changes
In case the child nameservers option is not available on your hPanel, or it doesn’t work, please contact our Customer Success team, and we will add the required child nameservers for you ?
Once that’s done, you will need to create A records for your new child nameservers. For that follow this procedure:
-
Copy your child nameserver IP or IP’s (if you used different ones)
-
Create new A records for each different IP child nameserver used:
|
NS 1 record |
NS 2 record |
NS 3 record (optional) |
NS 4 record (optional) |
|
Name: ns1 Points to: your child nameserver IP TTL: Default |
Name: ns2 Points to: your child nameserver IP TTL: Default |
Name: ns3 Points to: your child nameserver IP TTL: Default |
Name: ns4 Points to: your child nameserver IP TTL: Default
|
Any DNS Record changes trigger propagation, which can last up to 24 hours to fully propagate.
Contact with Me

Shaik Saimeeraa
Linux Server AdministratorThe best way to predict the future is to create it.
Phone: +917989390196 Email: info@shaiksaimeera.in